SYSTEMS CONSULTANT, MSP & SMB Owner of IAD SYSTEMS LLCsince 1996
New England: New York, Rhode Island, Connecticut & Massachusetts Areas
VPN Remote Systems Accessible & World-Wide On-Site Capable



Communicate: https://iadsystems.rocket.chat
(opens in new window)
Test passes if there is a permission prompt including the host and no FAIL.
Recent News on Technology, Privacy & Scientific Exploration:
- Everything you need to know about EARN IT, anti-encryption law now in Congress
- Everything you need to know about the LAED Act, anti-encryption law now in Congress
General Public Security Tips for September 2020
|
What is a "WebRTC leak (DNS Leak)"?WebRTC implement STUN (Session Traversal Utilities for Nat), a protocol that allows discovery of your public IP address.
What is a "DNS leak"?In this context, with "DNS leak" we mean an unencrypted DNS query sent by your system OUTSIDE the established VPN tunnel. Why my system suffers from DNS leaks?In brief: Windows lacks the concept of global DNS. Each network interface can have its own DNS. Under various circumstances, the system process svchost.exe will send out DNS queries without respecting the routing table and the default gateway of the VPN tunnel, causing the leak. Should I be worried about DNS leaks?If you don't want your ISP, and anybody with the ability to monitor your line, to know the names your system tries to resolve (so the web sites you visit etc.) you must prevent your system from leaking DNS. If you feel that you're living in a human rights hostile country, or in any way the above mentioned knowledge may harm you, you should act immediately to stop DNS leaks. |
How to create a bootable OS for almost any computer platformIt takes two downloads, you run Rufus, select the "image" file you downloaded, and once created, your USB Stick or CD/DVD will boot from just about any computer.
Why Would I want to use a portable bootable operating system with persistent encrypted storage?
|
How to use a search engine like a Professional, Efficiently...Expertly: [Boolean Searching]
Google and Bing Boolean Command Reference
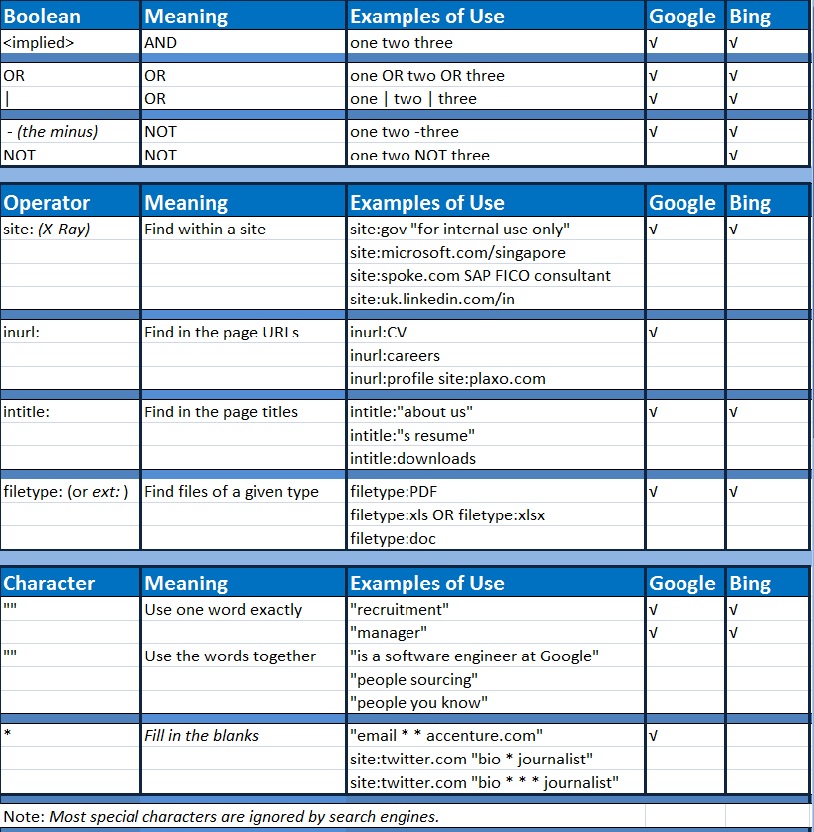
How To Google Search Boolean Ninja Style
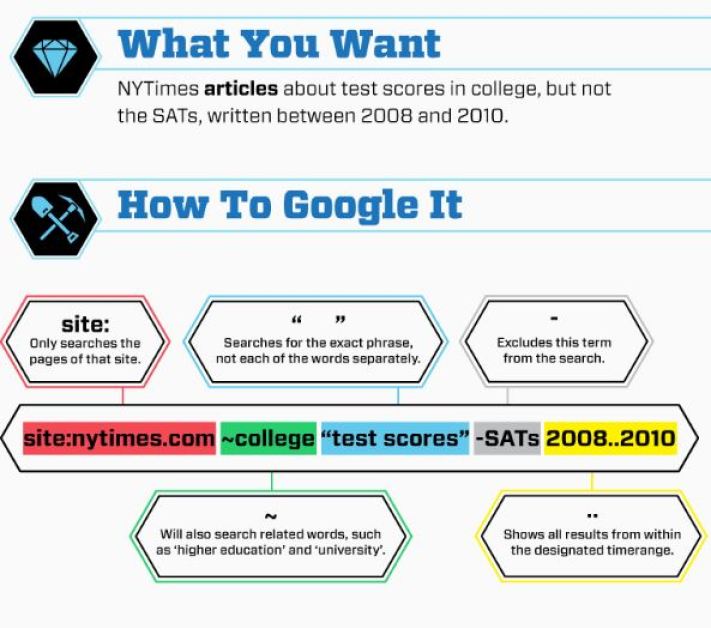
PSTN Telephone Cell Phone Number Breakdown
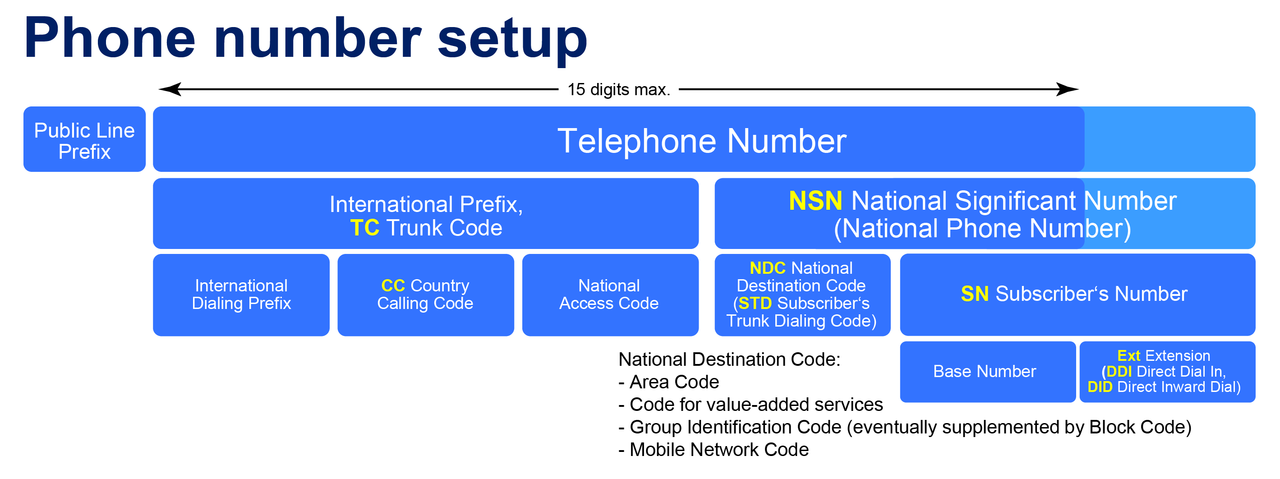
How Complicated is Authentication? It is NOT!
Secure an Android Cellular Telephone
Android phones can easily be secure, virtually impenetrable to hacks, cracks, and bad apk's (APPs) Even if you skip the entire set-up process and ignore every safeguard prompt, your Android phone still tries to keep information safe. google play protect IDG Google has built a malware scanner right into the Play Store called Play Protect. First and foremost, it runs a safety check on apps before you download them, but more importantly, it also checks your phone for any apps that may have gone awry since you downloaded them. If it finds any, it will warn you via a notification and in extreme cases delete them from your device on its own. You can check your Google Play Protect settings and see the apps it scanned in the Updates tab inside the My apps & games section of the Play Store. Encryption Ever since Android 5 Lollipop, Android has offered full-device encryption by default, as long as you set some kind of an locking method on your phone (pattern, pin, or password). In Android 7 Nougat, that switched to file-based encryption, but the end result is essentially the same:
The data on your phone is protected by 256-bit AES standard encryption as soon as its locked, so unless someone knows your passcode, they can’t see anything.
Android security: Basic protection
You don’t need to be a paranoid android to put a basic layer of protection on your device, you only need to change a few settings. Set a password While newer Android phones offer numerous biometric methods for unlocking, every phone still requires one of three traditional locking methods: pattern, PIN, or password. They’re not created equal, though. A pattern (made on a 9-dot square) is easiest to remember but the least secure. A 6-digit pin is far better, but the best of all is a random password. But even if you choose a string of letter and numbers, you should set a reminder to change once every six months or so. And make sure it’s not the same as the one that protects your primary Google account. Turn on 2-step verification No matter what you use your phone to do, your Google account is central to everything that happens. As the name suggests, with 2-step verification, you’re adding an extra layer of protection, so even if someone steals your password they still won’t be able to get into your account. Here’s how it works. After you’re prompted to enter your Google password, a code will be sent to your default phone via text or call which will need to be entered in order to grant access your account. While this won’t necessarily protect your phone against theft, it will protect what’s on it.
For example, if someone tries to remotely log in to your Google account from another device, you’ll know via the 2-step message on your phone. And then you can take the appropriate action and change your password. google find my device IDG Google offers a handy tool to track a lost or stolen phone right in the Play Store. Called Find My Device, it lets you track, lock, and erase your handset from wherever you are with just a tap. After downloading, you can sign in using your Google account and allow it to access your your device’s location. From then on, you’ll be able to log into Google’s Find My Device site and instantly locate where your phone is if you lose it. You’ll also be able to remotely lock your device, display a message or phone number for whomever finds it, or completely erase all of the content on your phone. Google releases monthly security updates for Android that most newer phones distribute in a relatively timely manner. You don’t need to check for them—once one is available, your phone will automatically let you know. But don’t delay, because it’s easy to forget about them. Set or schedule an update to be installed as soon as your phone lets you know it’s available. It only takes a few minutes and it could make all the difference.
Android security: Moderate protection
Now that the basic stuff is out of the way, let’s work on putting an even stronger lock on your Android phone. Set up fingerprint unlock google pixel imprint IDG A password might be a strong way to secure your phone, but it can’t beat your fingerprint. And if you bought your Android phone within the past two years, there’s a good chance it has a fingerprint sensor either below the screen, on the back, or built into the power button. Find it and head over to your security settings to register one or more fingerprints. It only takes a few seconds to enact a very important layer of protection. Numerous phones also offer face unlocking, but unless you have a Huawei Mate 20, you should skip these. That’s because most phones use the 2D front camera to scan your face rather than a 3D map like with Face ID on the iPhone or Huawei’s depth-sensing camera, so they’re very easy to spoof with little more than a picture. Prevent unknown downloads One of the greatest benefits of Android is also one of it’s biggest risks: downloading apps that aren’t on the Play Store. When you install an app from outside Google’s store, you’re losing out on Play Protect and opening your phone up to possible malware. To keep a lid on any potential trouble, Google has built a way to shut off any accidental or unintentional downloads. In the Special app access settings, you’ll find an Unknown sources or Unknown apps tab, which lets you shut off the installation of apps from a non-Play Store source, such as Chrome or some other browser. android unknown apps IDG Depending on your phone, the mechanism is a little different. Up until Android Nougat, there was a single toggle that let you either block or install apps from unknown sources. In Android Oreo and later, permission is granted on a per-app basis, so you can allow Chrome or Slack to install apps while blocking others. It’s a good habit to visit this setting every once in while to make sure there aren’t any malicious apps that are allowed to install software behind the scenes. If you find any that are, tap the name and turn the toggle off. Uninstall apps Speaking of wayward apps, one of the best ways to keep your system safe is good, old-fashioned house cleaning. Simply jump into your app drawer and simply uninstall apps that you haven’t used in a while. It’ll free up storage and it’ll make sure they don’t turn into potential risks.
Check app permissions
It’s also a good idea to check in on your app permissions every now and again. When you download an app from the Play Store and launch it for the first time, Android asks you if it can have access to things like the microphone, camera, phone, etc. A lot of times we just tap away access without even realizing what they’re asking for, but you can always of back and revoke it after the fact. Head over to the Permissions tab inside Apps in Settings and you’ll be able to see which apps are allowed to do what—and turn off anything that looks suspicious.
Android Security: High protection
If you came here to learn how to turn your Android phone into a vault, here’s what you need to do. Disable Smart Lock for Passwords and Auto Sign-in Smart Lock for Passwords might be convenient, but if you want to lock down your phone, you’re going to need to handle your passwords on your own. And that unfortunately means turning off Smart Lock for Passwords. Here’s why: Google’s method doesn’t use any kind of authentication on a per-site or account basis like password managers do, so after signing in to your account for the first time on your device, all of your passwords will be available. That obviously could be a problem if someone swipes your phone. google smart lock IDG You’ll find the toggle inside the security settings for your Google account, not inside the Security tab in Settings. Once you get there, tap on Security, then scroll down to Signing in to other sites, and tapped Saved Passwords. You’ll see two toggles: Offer to save passwords and Auto sign-in. If you don’t want to turn the whole thing off, you can also select sites that ignore auto sign-in. We think a much better solution would be to require biometric authentication every time a password is entered (which Apple does on the iPhone), so until that happens, you should switch it off if you’re paranoid. Download a password manager If you’re turning off Smart Lock, the only way to keep your passwords safe and organized is to lock them up inside a password manager. Stronger and more secure than the Smart Lock password sync Google offers, a password manager encourages unique, complex passwords, lets you organize and manage multiple logins, and stores sensitive notes, credit card information, and anything else you want to keep in a digital locker. And it’s all protected by a password or a fingerprint, whichever you choose. LastPass Since your password mananger is a separate service, you’ll be able to access your passwords on any device or browser, so even if someone steals your phone your most personal data will still be protected. With Android Oreo, you’ll even be able to incorporate some of them into Autofill on your phone (fingerprint-protected, of course).
Use a
VPN: Mullvad Check Your Connection
No matter how many safeguards you add to your phone, it’s inherently vulnerable every time you visit the web. Why? Because the information you send can be stolen and spied on with little effort, especially if you’re using a public Wi-Fi hotspot. If you use a VPN service, your information is encrypted before it hits the airwaves, so your data is fully protected from everybody except the VPN provider and whatever website you're visiting. Even if someone manages to steal it, it’s protected. There are numerous VPNs in the Play Store, so make sure you check out the rankings and user reviews before making your pick. Our recommendation for starting out is TunnelBear, which is free and super simple. If you’re looking for something more advanced, you can download OpenVPN for Android and experiment with Mullvad, the top PC pick in our roundup of the best VPN services.
Use an Authenticator app We’ve already discussed how important 2-step verification is for your Google account, but you should also be using it for any service that offers it: Twitter, Facebook, Dropbox, etc. But if you want to take it one step further, you can use an authenticator app to generate unique codes right on your phone rather than sending them over SMS text messages, which can be riskier. Google makes its own authenticator app for your Google account and many other sites that’s free in the Play Store, so we recommend checking it out. Get a physical security key google titan security key Google
If you want the ultimate protection for your accounts, nothing beats an NFC security key. Roughly the size of a flash driven (so you can attach it to a keychain) and completely phishing-proof, a security key dispenses with codes and stores all of your authentication on a physical device. So it’s basically impossible to get into any of your accounts without the key, even if someone manages to steal all of your passwords. The $50 Titan Security Key bundle (which includes USB and Bluetooth security keys) is a great option from Google, but there are options from Yubico
Enter Lockdown mode If all else fails, Google has added a new Lockdown option to Android 9 that lets you completely secure your phone at a tap. Hold down the power button for a second and you’ll see a Lockdown option at the bottom of the list. (If you don’t, you can enable it in the Lock screen settings.) Tap it and your phone will instantly lock, turn off the fingerprint scanner (so someone can’t force your finger to unlock it), remove all notifications from the lock screen, and disable Smart Lock. And it’ll stay that way until the next time you re-lock your phone.
Inquire via Base64 Decode: data:text/plain;base64,Um9iZXJ0IEogUGxvb2YsIElBRCBTWVNURU1TIExMQzogPHNlY3VyaXR5QGlhZHN5c3RlbXMuY29tPiArMSAoOTQxKSA0ODctMDA0MQ==
Copyright Intellectual Property © 1996 - 2020 IAD SYSTEMS LLC
This IAD SYSTEMS LLC document and translations of it may be copied and furnished to others, and derivative works that comment on or otherwise explain it or assist in its implementation may be prepared, copied, published and distributed, in whole or in part, without restriction of any kind, provided that the above copyright notice and this paragraph are included on all such copies and derivative works. This document itself may not be modified in any way.

